- Home Page
- Company Profile
-
Our Products
- Motorized CCTV Camera
- Analog IR Night Vision Motorized Varifocal Bullet Camera
- IP Varifocal Motorized Zoom Bullet Camera
- IP Motorized CCTV Camera
- Smart Varifocal Motorized Zoom Bullet Camera
- Smart IP Varifocal Motorized Zoom Dome Camera
- IP Night Vision Smart Varifocal Motorized Zoom Dome Camera
- Array Night Vision Smart Varifocal Motorized Bullet Camera
- IR Night Vision Smart Varifocal Motorized Zoom Dome Camera
- 60 FPS IP Night Vision Smart Varifocal Motorized Zoom Camera
- 60 FPS IP Night Vision Smart Varifocal Motorized Dome Camera
- IP Array IR Night Vision Smart Varifocal Motorized Zoom Camera
- IR Night Vision Smart Varifocal Motorized Zoom Camera
- Motorized Network Camera
- IP Night Vision Varifocal Motorized Zoom Dome Camera
- CS Mount Camera
- AHD DVR
- Turnstile Gates
- PTZ Dome Camera
- Security Alarm Accessories & Sensors
- Biometric Machine
- IP Varifocal Camera
- Array IR Full HD Varifocal Camera
- Electronic Boom Barriers
- Swing Gate Barriers
- Video Door Phone
- Array IR Full HD Camera
- 5 in 1 DVR
- Vehicle DVR
- RFID Systems
- Special Application Cameras
- Smart Wi-Fi Fixed Camera
- IR Night Vision Smart Fixed Camera
- Network Video Recorder
- HD TVI DVR
- Analogue Cameras
- Network Cameras
- Digital Video Recorder
- Video Door System
- Surveillance Equipment Parts
- Network Video Recorders
- IR Night Vision HD Camera
- IR Night Vision Varifocal HD TVI Camera
- Pan Tilt Camera
- RFID Controllers
- Audio Door Phone
- Biometric Access Control System
- Wireless Alarm Systems
- Licence Plate Recognition Camera
- Fingerprint Identification Systems
- Alarm Systems
- Guard Monitoring System
- Flap Barrier
- RFID Access Control System
- RFID Reader
- Array IR Night Vision Fixed Camera
- Motorized CCTV Camera
- Extra Links
- Contact Us
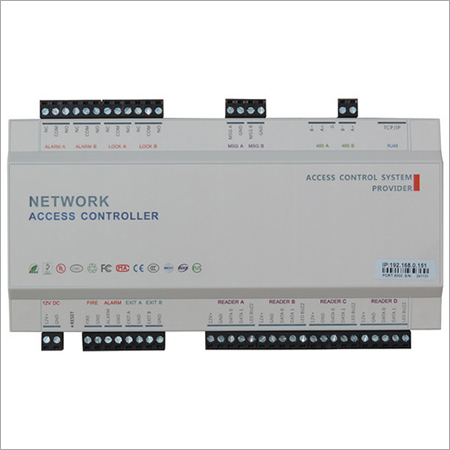
Two Door Two Way RFID Controller
15184.00 - 18688.00 INR
Product Details:
- Connectivity Type TCP/IP, RS485, Wiegand Input/Output
- Sensor Type RFID Card Reader Module, Exit Button Sensor
- Technology RFID, Microcontroller Based Embedded System
- Special Features Two Door Access, Two Way RFID control, Anti-Passback, Real-time Monitoring, Event Log Storage, Tamper Alarm, Fire Alarm Integration
- Remote Control Supported via Ethernet/Network
- Application Office, Industrial Complex, Secure Facilities, Data Centers
- Power Supply DC 12V / 2A
- Click to View more
X
Two Door Two Way RFID Controller Price And Quantity
- 15184.00 - 18688.00 INR
- 5 Piece
Two Door Two Way RFID Controller Product Specifications
- Supported via Ethernet/Network
- Two Door Access, Two Way RFID control, Anti-Passback, Real-time Monitoring, Event Log Storage, Tamper Alarm, Fire Alarm Integration
- TCP/IP, RS485, Wiegand Input/Output
- Event Log CSV, Alarm Notification Signals
- Proprietary Access Control Database
- Office, Industrial Complex, Secure Facilities, Data Centers
- DC 12V / 2A
- RFID Card Reader Module, Exit Button Sensor
- RFID, Microcontroller Based Embedded System
Two Door Two Way RFID Controller Trade Information
- Can Supply Maximum Number of Products in the delivery time Per Week
- Maximum 1 Week Week
Product Description
Technical Specification
| Parameter | Specifications | |
| User capacity | 30000 users | |
| Transaction capacity | 60000 logs | |
| Alarm event | 60000 logs | |
| Communication | TCP/IP and RS-485 | |
| Communication distance | Software management without limitation | |
| Card Reader supported | Wiegand protocol | |
| Door open method
| ||
| CPU | 32 bit 400MHz CPU | |
| Working temperature
| ||
| Humidity | 10% to 95% R.H | |
| Working voltage | 12V DC | |
| Working current | <240mA | |
| Rated power | <5w | |
| Panel dimension | 232x134x22mm | |
| Package weight | 1.4kg | |
| Data protection if no power supply | 10 years | |
| Standard interface | ||
| Card reader | 4 No. | |
| Fire alarm in/out | 1No. | |
| alarm in/out | 1 No. | |
| Lock release button input | 2 No. | |
| Door sensor input | 2 No. | |
| Lock output | 2 No. | |
| TCP/IP communication | 1 No. | |
Scalable and Versatile Access Control
With support for up to 30,000 users and 100,000 event logs, this controller addresses the needs of growing organizations, seamlessly adapting to evolving infrastructure. The dual-door, dual-way functionality enables advanced monitoring and secure entry/exit management, while the four relay outputs allow integration with locks and alarms for heightened premises protection.
Robust Industrial Design
Housed within a durable industrial-grade metal enclosure, the RFID controller is engineered to withstand challenging environments, functioning reliably across a temperature range of -10C to +60C. The compact form factor (210 mm x 175 mm x 45 mm) and substantial build quality (approx. 1.8 kg) ensure long-lasting performance and ease of installation in offices, data centers, or secure industrial locations.
Comprehensive Integration & Connectivity
Designed for flexibility, the controller supports multiple connectivity options, including TCP/IP, RS485, and Wiegand input/output, along with proprietary database compatibility. Network-based firmware upgrades, real-time event monitoring, and remote control functionality facilitate smooth integration into existing security ecosystems, ensuring continuous protection and streamlined management.
FAQs of Two Door Two Way RFID Controller:
Q: How does the Two Door Two Way RFID Controller ensure secure access management?
A: This controller provides secure access management through two-way, dual-door RFID control, supporting anti-passback features, real-time monitoring, tamper detection, and alarm integration. These capabilities work together to prevent unauthorized entry and ensure accurate tracking of entry and exit events.Q: What is the process for adding or removing users from the system?
A: Users can be added or removed via the systems proprietary access control software, which connects to the controller through TCP/IP or RS485 interfaces. The administrator uploads user data, assigns appropriate access permissions, and synchronizes the updates, allowing the system to support up to 30,000 users efficiently.Q: When should I use the optional backup battery feature?
A: The optional backup battery is recommended for environments where uninterrupted access control is critical, such as data centers and secure industrial sites. It ensures continuous operation during power outages, maintaining door control, event logging, and alarm functionality until normal power is restored.Q: Where can this RFID controller be installed for optimal performance?
A: This device is ideal for installation in offices, industrial complexes, data centers, and secure facilities. Its robust enclosure and wide operating temperature range make it suitable for diverse indoor locations that require strict access control and reliable event monitoring.Q: How do the relay outputs and input ports enhance security?
A: The controller offers four relay outputs for integrating with electric locks and alarm systems, plus four input ports for door sensors and exit buttons. This arrangement enables automated locking, real-time alarm triggering, and immediate response to tampering or unauthorized actions, significantly boosting overall security.Q: What are the benefits of real-time event log storage and monitoring?
A: With storage for up to 100,000 event records and real-time monitoring capabilities, administrators gain immediate insights into all access activities. This facilitates prompt detection of security breaches, simplifies auditing processes, and supports comprehensive incident investigations, enhancing operational transparency.Tell us about your requirement

Price:
Quantity
Select Unit
- 50
- 100
- 200
- 250
- 500
- 1000+
Additional detail
Mobile number
Email